- ERC20 & ERC721 tokens (for EVM-compatible chains)
- SVM-based assets (for SVM-compatible chains)
- Native tokens (such as ETH, or other gas tokens)
Modular Security
Like all applications built on top of Hyperlane, HWRs have customizable security via Interchain Security Modules. The deployer of a HWR can specify the ISMs that are used to verify interchain transfer messages. This means that each HWR may have a unique security configuration. Users transferring interchain tokens should understand the trust assumptions of a Route before using it.Similarly, Warp frontends should manually curate their HWR to avoid supporting
insecure ones. See the Warp UI deployment
docs details.
HWR Architecture
HWR let deployers choose how tokens are transferred between chains. Depending on the type of HWR, contracts will lock tokens, mint wrapped tokens, burn wrapped tokens, or release original tokens. For example:- Collateral → Synthetic: Tokens are locked on the origin (collateral) chain, a message is sent, and wrapped tokens are minted on the destination (synthetic) chain.
- Native → Synthetic: Native gas tokens (e.g., ETH) are locked on the origin chain, a message is sent, and synthetic tokens are minted on the destination chain.
- Native → Collateral: Native tokens are locked on the origin chain, a message is sent, and collateral tokens are released on the destination chain.
HWR Types
This table gives a high-level overview of HWR types. For detailed explanations, see: HWR Types.| HWR Type | Description |
|---|---|
| Native Token HWRs | Enables direct transfers of native gas tokens (e.g., ETH) across chains without wrapping. |
| Collateral-Backed ERC20 | Locks ERC20 tokens as collateral on the source chain for cross-chain transfers. |
| Synthetic ERC20 | Mints new ERC20 tokens on the destination chain to represent the original tokens. |
| Hyperlane Warp Routes 2.0 | Allows liquidity to be sourced from multiple collateral tokens. |
| Specialized HWR | Adds advanced features or integrates with specific use cases (e.g., vaults, fiat-backed tokens.) |
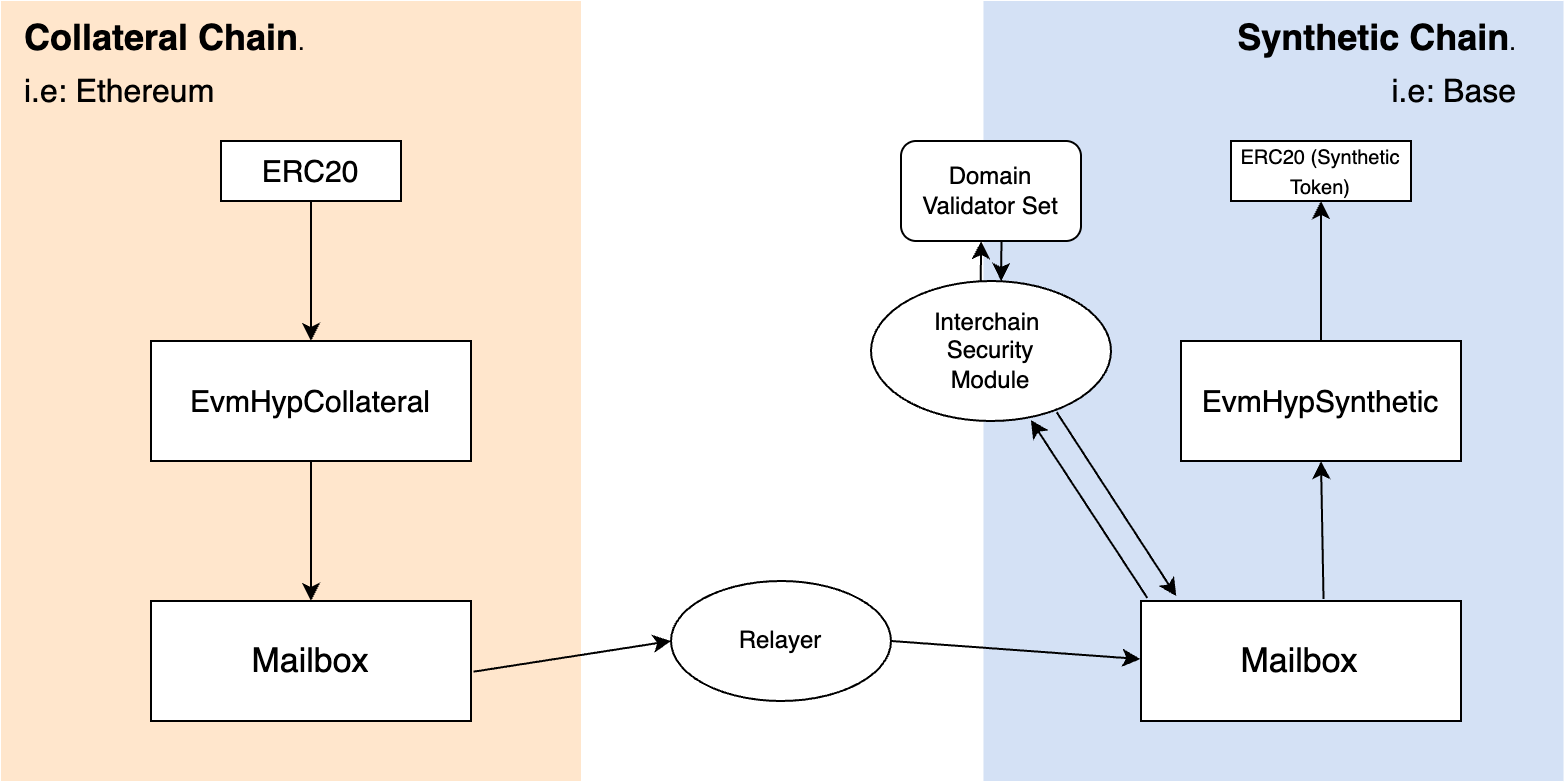
Example Architecture
Let’s walk through a Collateral to Synthetic HWR using the lock-and-mint model to transfer ERC20 tokens between two chains:- The user locks their tokens on the collateral chain (e.g., Ethereum) in the HWR contract.
- A message is sent through Hyperlane’s Mailbox and relayed to the synthetic chain (e.g., Base).
- On the destination chain, the HWR contract mints wrapped tokens to the user.